Your Software token model images are ready. Software token model are a topic that is being searched for and liked by netizens today. You can Download the Software token model files here. Download all royalty-free images.
If you’re searching for software token model pictures information linked to the software token model topic, you have come to the right site. Our website frequently provides you with suggestions for refferencing the maximum quality video and image content, please kindly surf and find more enlightening video content and images that fit your interests.
Software Token Model. It is quite a popular and advanced software which is used in 3D Modeling 3D animation 2D animation Simulation VFX Game Creation Video Editing Rendering Scripting etcYou can do a lot of things including 3D character creation with this but it is quite difficult to create 3D characters with this software. With the New Commercial Model users can take advantage of the integrated functionalities in the entire aspenONE Engineering Suitewithout individual product licenses. Supports up to 10 software tokens per device. Strong two-factor authentication to protected services.
 The Security Token Ecosystem Tokeny Solutions From tokeny.com
The Security Token Ecosystem Tokeny Solutions From tokeny.com
The Rally project has launched social tokens for 180 creators and rewarded the equivalent of 28 million to those creators and their communities. Available in 8 languages. Deliver greater innovation and higher quality at lower cost. Today the RSA SecurID hardware token comes in a pair of convenient models that all generate and display new codes ev ery 60 seconds. The model for PKCS11 can be seen illustrated below demonstrating how an application communicates its requests to a token via the PKCS11 interface. Keywords hardware tokens two-factor authentication RSA SecurID key fob.
The simplest form of token software license model is implemented and easiest described as a variant of a floating license model.
For example a smart card reader would represent a slot and the smart card would represent the token. When the circulation quantity of JUB is less than 5 million. Token licenses are in fact a form of Network Floating licenses only that instead of having a pool of licenses they have a pool of tokens. Today the RSA SecurID hardware token comes in a pair of convenient models that all generate and display new codes ev ery 60 seconds. The PKCS11 Model. The software tokens can be installed on a users desktop system in the cellular phone or on the smart phone.
 Source: cxf.apache.org
Source: cxf.apache.org
App available for download through the Apple App Store. The practice of licensing portfolios of applications typically through consuming a shared pool of tokens which represents an overall annual investment in a vendors software. Deliver greater innovation and higher quality at lower cost. Token import log for troubleshooting. Fyooz operates a token marketplace.
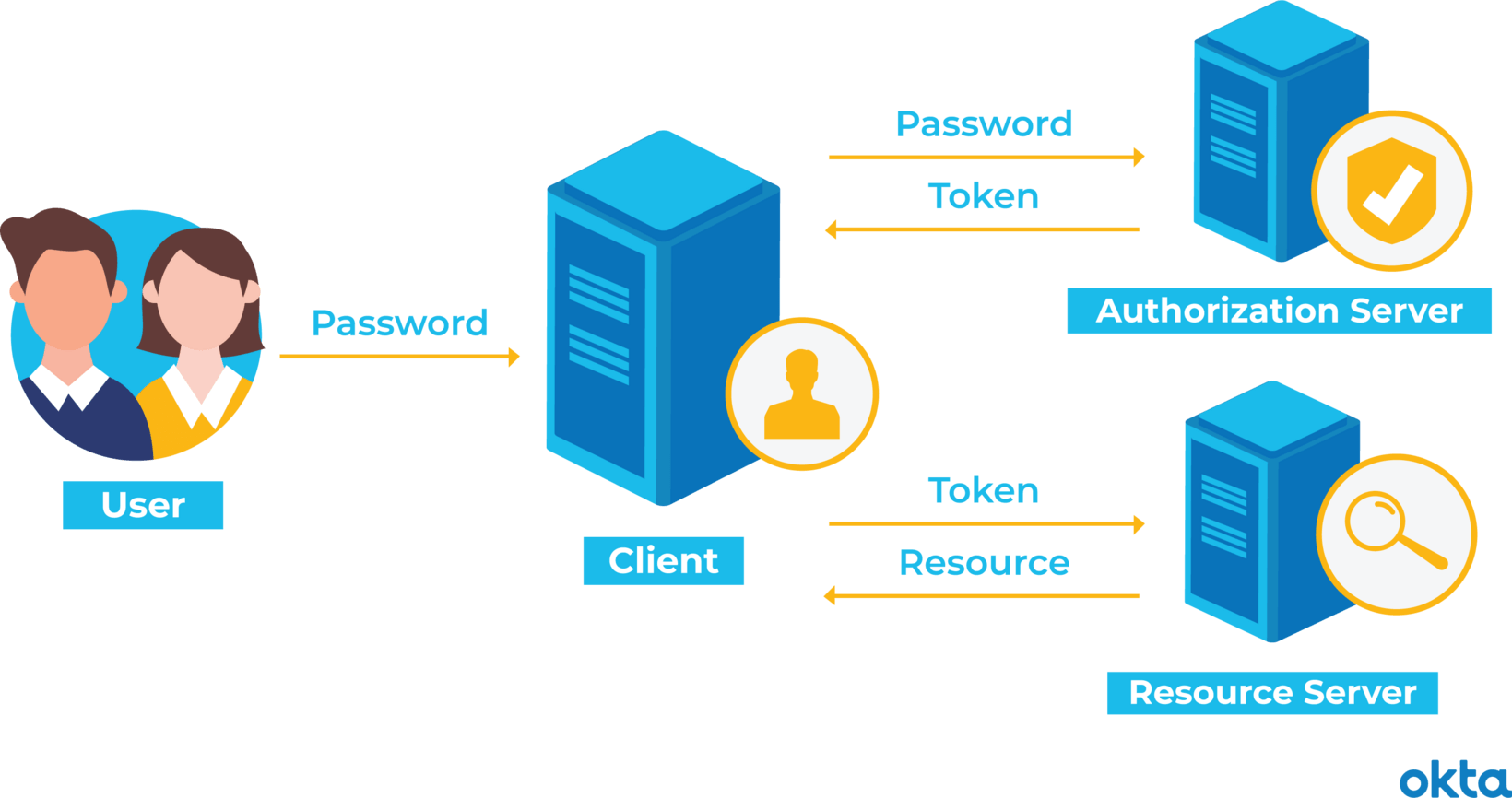 Source: okta.com
Source: okta.com
Different applications within the portfolio may consume varying numbers of tokens depending on value. The practice of licensing portfolios of applications typically through consuming a shared pool of tokens which represents an overall annual investment in a vendors software. Strong two-factor authentication to protected services. There are both software and hardware tokens. The Token licensing model allows you to buy a certain number of tokens for defined products available with the token-based licensing model.
 Source: embedded.com
Source: embedded.com
The practice of licensing portfolios of applications typically through consuming a shared pool of tokens which represents an overall annual investment in a vendors software. With the New Commercial Model users can take advantage of the integrated functionalities in the entire aspenONE Engineering Suitewithout individual product licenses. Fyooz operates a token marketplace. Token provisioning from QR Code URL link or file attachment. The number of consumed tokens is specific to each feature and is apparent in the featureIncrement line in the license file.
 Source: aws.amazon.com
Source: aws.amazon.com
Token holders are given the authority to verify and add transactions to the distributed ledger algorithmically based on proportions of tokens held. A token is a device that employs an encrypted key for which the encryption algorithmthe method of generating an encrypted passwordis known to a networks authentication server. The simplest form of token software license model is implemented and easiest described as a variant of a floating license model. Convert iMed files to generic 3D file formats. New tokens are launched by protocol 90 will be given to stakers and bonds 6 will belong to expenses of team and hardware and software 3 will be used for expenses such as marketing currency exchange and auditing and 1 will be used for DAO.
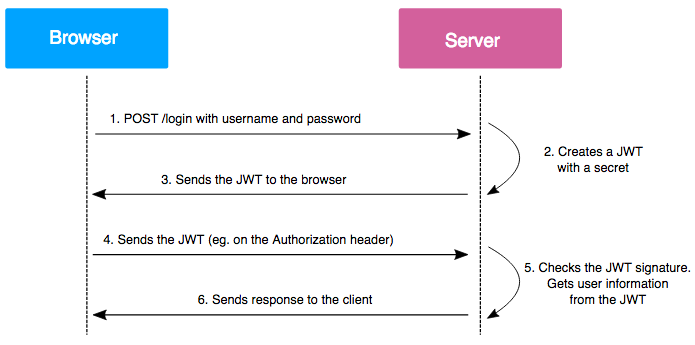 Source: vaadata.com
Source: vaadata.com
Buy tokens to start scanning and only pay for what you really need and the files you really use. For example a smart card reader would represent a slot and the smart card would represent the token. The model for PKCS11 can be seen illustrated below demonstrating how an application communicates its requests to a token via the PKCS11 interface. Token licenses are in fact a form of Network Floating licenses only that instead of having a pool of licenses they have a pool of tokens. Pay-per-Scan model for MSoft license.
 Source: e-zigurat.com
Source: e-zigurat.com
The term slot represents a physical device interface. Different applications within the portfolio may consume varying numbers of tokens depending on value. Today the RSA SecurID hardware token comes in a pair of convenient models that all generate and display new codes ev ery 60 seconds. AspenONE Engineering is an integrated suite of software. 25 100 CAD.
 Source: tokeny.com
Source: tokeny.com
With the New Commercial Model users can take advantage of the integrated functionalities in the entire aspenONE Engineering Suitewithout individual product licenses. 132 Token Count means the number of Tokens required to operate a single instance of a Software product in accordance with the applicable Unit of Measure specified in the Token Count Table. Convert iMed files to generic 3D file formats. Buy tokens to start scanning and only pay for what you really need and the files you really use. The PKCS11 Model.
Source: encrypted-tbn0.gstatic.com
With NX you can use the most productive modeling approaches interchangeably from explicit solid and surface modeling to parametric and direct modeling along with facet-based modeling. The practice of licensing portfolios of applications typically through consuming a shared pool of tokens which represents an overall annual investment in a vendors software. Today the RSA SecurID hardware token comes in a pair of convenient models that all generate and display new codes ev ery 60 seconds. Available in 8 languages. Pay-per-Scan model for MSoft license.
Source: micobo.medium.com
Strong two-factor authentication to protected services. SecurID Software Token for iOS. Today the RSA SecurID hardware token comes in a pair of convenient models that all generate and display new codes ev ery 60 seconds. Long before introducing the software token or tokenless risk-based. When a feature is checked-out a certain amount of tokens are consumed.
 Source: curity.io
Source: curity.io
Prepaid token model. When a feature is checked-out a certain amount of tokens are consumed. Pay-per-Scan model for MSoft license. When the circulation quantity of JUB is less than 5 million. With NX you can use the most productive modeling approaches interchangeably from explicit solid and surface modeling to parametric and direct modeling along with facet-based modeling.

App available for download through the Apple App Store. Strong two-factor authentication to protected services. Buy tokens to start scanning and only pay for what you really need and the files you really use. For example if Microsoft Office were. Tokens are licensed to create a token pool for your company.
 Source: embedded.com
Source: embedded.com
SecurID Software Token for iOS. When a feature is checked-out a certain amount of tokens are consumed. Start designing in minutes. Prepaid token model. Convert iMed files to generic 3D file formats.
 Source: docs.microsoft.com
Source: docs.microsoft.com
133 Token Count Table means the schedule of Software products and associated Token Counts and Units of Measure that is attached to the Cover Page. Release Download RSA SecurID Software Token 502 for Microsoft Windows 64-bit SHA256. Token provisioning from QR Code URL link or file attachment. The token software license model makes it financially easy for the customer to utilize the entire portfolio of software and not try to buy the best-of-breed for every part of a design flow. 25 100 CAD.
 Source: hedera.com
Source: hedera.com
The model produces a sensitivity analysis estimating at 5 adoption of the primary TAM by 2030 risky enough to justify a 26 discount rate for present value calculations the token price of. The model for PKCS11 can be seen illustrated below demonstrating how an application communicates its requests to a token via the PKCS11 interface. Available in 8 languages. Token provisioning from QR Code URL link or file attachment. The Rally project has launched social tokens for 180 creators and rewarded the equivalent of 28 million to those creators and their communities.
 Source: pinterest.com
Source: pinterest.com
Token licenses are in fact a form of Network Floating licenses only that instead of having a pool of licenses they have a pool of tokens. Release Download RSA SecurID Software Token 502 for Microsoft Windows 64-bit SHA256. It is quite a popular and advanced software which is used in 3D Modeling 3D animation 2D animation Simulation VFX Game Creation Video Editing Rendering Scripting etcYou can do a lot of things including 3D character creation with this but it is quite difficult to create 3D characters with this software. When a feature is checked-out a certain amount of tokens are consumed. Deliver greater innovation and higher quality at lower cost.
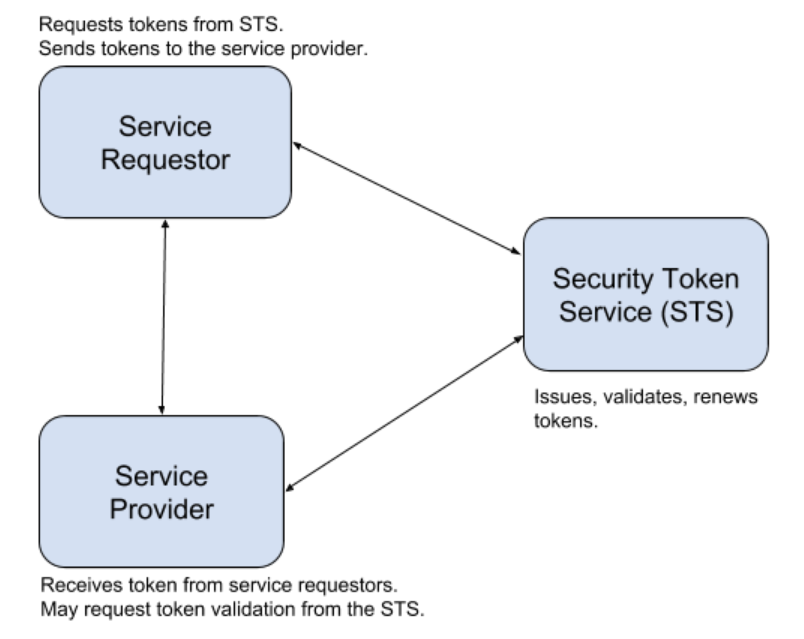 Source: medium.com
Source: medium.com
The model produces a sensitivity analysis estimating at 5 adoption of the primary TAM by 2030 risky enough to justify a 26 discount rate for present value calculations the token price of. 133 Token Count Table means the schedule of Software products and associated Token Counts and Units of Measure that is attached to the Cover Page. App available for download through the Apple App Store. Available in 8 languages. New tokens are launched by protocol 90 will be given to stakers and bonds 6 will belong to expenses of team and hardware and software 3 will be used for expenses such as marketing currency exchange and auditing and 1 will be used for DAO.
 Source: sciencedirect.com
Source: sciencedirect.com
Tokens are licensed to create a token pool for your company. It is quite a popular and advanced software which is used in 3D Modeling 3D animation 2D animation Simulation VFX Game Creation Video Editing Rendering Scripting etcYou can do a lot of things including 3D character creation with this but it is quite difficult to create 3D characters with this software. With the New Commercial Model users can take advantage of the integrated functionalities in the entire aspenONE Engineering Suitewithout individual product licenses. Token import log for troubleshooting. The practice of licensing portfolios of applications typically through consuming a shared pool of tokens which represents an overall annual investment in a vendors software.
 Source: doubleoctopus.com
Source: doubleoctopus.com
The practice of licensing portfolios of applications typically through consuming a shared pool of tokens which represents an overall annual investment in a vendors software. Keywords hardware tokens two-factor authentication RSA SecurID key fob. There are both software and hardware tokens. For example a smart card reader would represent a slot and the smart card would represent the token. License software in a modern way.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site good, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title software token model by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.







