Your Software token mfa images are available. Software token mfa are a topic that is being searched for and liked by netizens today. You can Find and Download the Software token mfa files here. Find and Download all royalty-free photos.
If you’re searching for software token mfa pictures information related to the software token mfa topic, you have visit the right site. Our website always provides you with suggestions for refferencing the highest quality video and picture content, please kindly search and locate more informative video content and images that match your interests.
Software Token Mfa. Generally the authenticator apps work on a shared secret key known by the. Verify the token received from the use. Response clientassociate_software_token AccessTokenuser_as_json access_token Which return a secret code. Order Tokens Directly from Duo.
 Would You Like Your Tokens Hard Or Soft Aspectra Hosting Your Future From aspectra.ch
Would You Like Your Tokens Hard Or Soft Aspectra Hosting Your Future From aspectra.ch
The next step was to steal an RSA SecureID Software Token. Duos D-100 tokens have an expected minimum battery lifetime of 2 years. To make use of one of these youll need Azure AD Premium P1 or P2 license. A premium Azure license is not required. Apps are software which means that wed be using software tokens. Next you can enable TOTP MFA for your user or.
Generally the authenticator apps work on a shared secret key known by the.
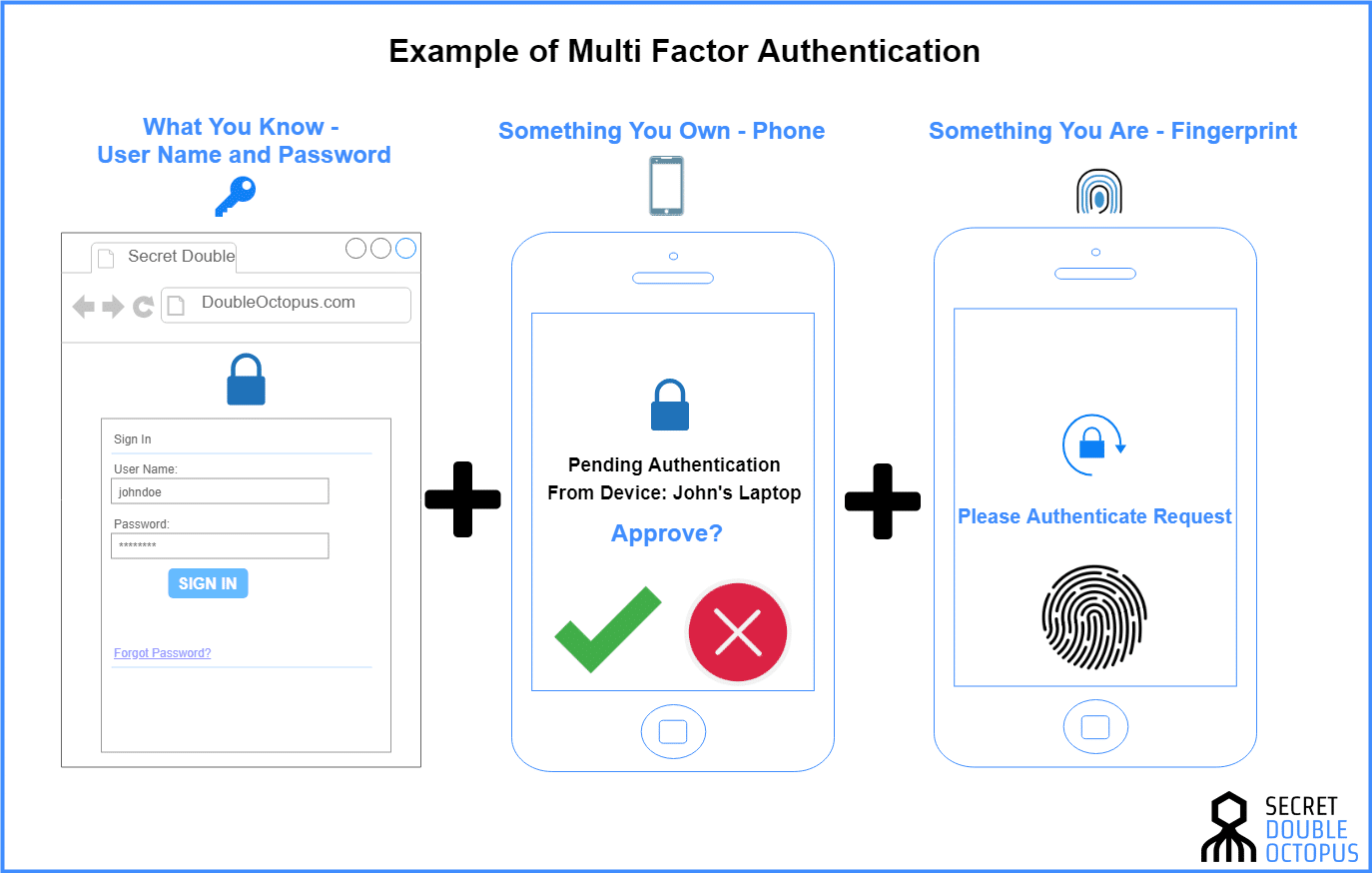
Streamlined end-user MFA experience Office 365 SAML Connector Standard SAML 20 integration via Active Directory Authentication Libraries ADAL Supports newer web and rich clients such as Office 2013 and subsequent editions Office 365 STS Connector Security Token Service STS model with Web Services Federation WS-Federation. Configuring TOTP for your user is a multi-step process where your user receives a secret code that they validate by entering a one-time password. Multi-factor authentication is the difference between for example entering a password to gain access and entering a password plus a one-time password OTP or a password plus the answer to a security. Multi-Factor Authentication MFA A strong foundation for secure access communications and data starts with trusted identities and ends with protecting your enterprise customers and partners while keeping friction to a minimum. To assign the tokens to users edit that file to add your users user principal names usually their email address and then upload it to Azure Porta l Azure Active Directory MFA Server OATH tokens. Duos D-100 tokens have an expected minimum battery lifetime of 2 years.

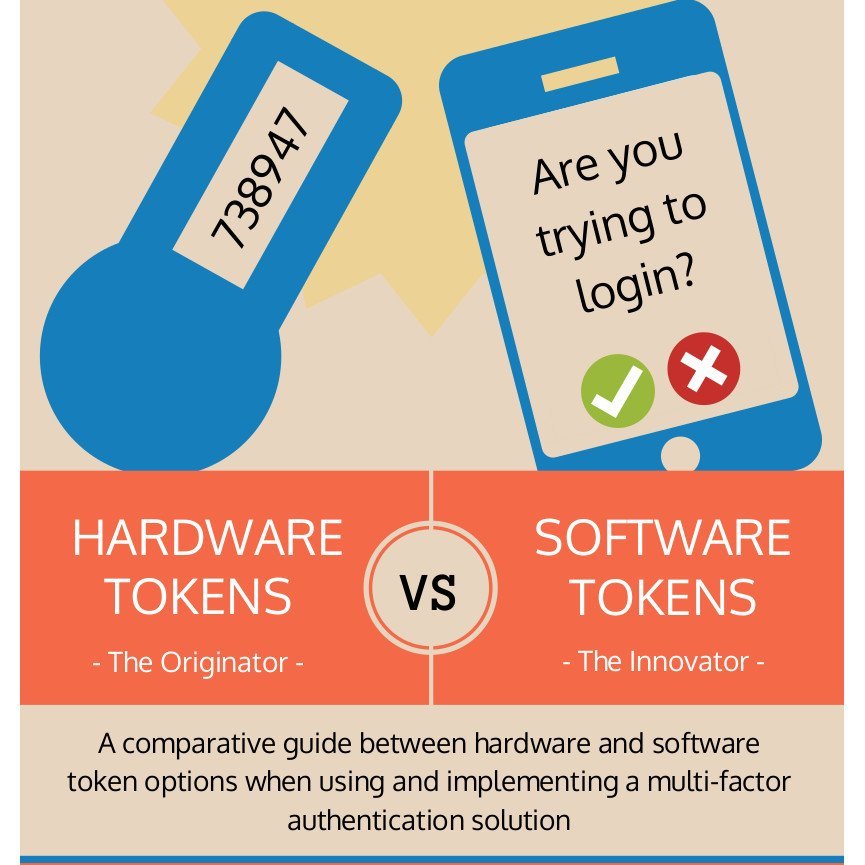
Next you can enable TOTP MFA for your user or. Generally the authenticator apps work on a shared secret key known by the. Duo is engineered to provide a simple streamlined login experience for every user and application and as a cloud-based solution it integrates easily with your existing technology. This type of token is used to generate valid one-time codes for MFA purposes. They have their pros and cons.
 Source: hideez.com
Source: hideez.com
This type of token is used to generate valid one-time codes for MFA purposes. Make sure to use the format described in the docs the secret is in base 32. Apps are software which means that wed be using software tokens. Streamlined end-user MFA experience Office 365 SAML Connector Standard SAML 20 integration via Active Directory Authentication Libraries ADAL Supports newer web and rich clients such as Office 2013 and subsequent editions Office 365 STS Connector Security Token Service STS model with Web Services Federation WS-Federation. The design and dimensions of this Microsoft Office 365 MFA hardware token are also a factor in its popularity.
 Source: sapikuda.com
Source: sapikuda.com
They are only available in. Third-party hardware tokens can be imported into the system by an administrator. Verify the token received from the use. MFA basics A simple password doesnt cut it for most systems especially ones with higher risks or sensitivity attached to them. Hardware Tokens MFA Agents macOS Microsoft Windows SecurID SDK Software Tokens Android Blackberry Blackberry 10 iOS macOS Token Converter Windows Windows Phone Downloads Authentication Agents API SDK Apache Web Server Citrix StoreFront IIS Web Server Microsoft AD FS Microsoft Windows PAM Authentication Engine Authentication Manager Cloud.
 Source: blog.identityautomation.com
Source: blog.identityautomation.com
However when specifying only SOFTWARE_TOKEN_MFA as the enabled MFA without any SMS the configuration should be. They have their pros and cons. This type of token is used to generate valid one-time codes for MFA purposes. AWS Cognito TOTP Software Token MFA Using Java Configuring TOTP for your user is a multi-step process where your user receives a secret code that they validate by entering a one-time password. I got below error.
 Source: blog.kloud.com.au
Source: blog.kloud.com.au
With classic OATH tokens for Azure MFA with hard-coded secret keys such as Protectimus Two and Protectimus Crystal. Configuring TOTP for your user is a multi-step process where your user receives a secret code that they validate by entering a one-time password. To assign the tokens to users edit that file to add your users user principal names usually their email address and then upload it to Azure Porta l Azure Active Directory MFA Server OATH tokens. Duo is engineered to provide a simple streamlined login experience for every user and application and as a cloud-based solution it integrates easily with your existing technology. Third-party hardware tokens can be imported into the system by an administrator.

To assign the tokens to users edit that file to add your users user principal names usually their email address and then upload it to Azure Porta l Azure Active Directory MFA Server OATH tokens. To protect your data with our OATH hardware token for Office 365 MFA you need to own an Office 365 subscription with 2-factor authentication on and an NFC Android phone. The next step was to steal an RSA SecureID Software Token. Order Tokens Directly from Duo. With a programmable hardware token for Azure MFA Protectimus Slim NFC which is a replacement for an authentication app from Microsoft.
 Source: doubleoctopus.com
Source: doubleoctopus.com
Hence we should focus on using smartphones as MFA devices. Users who have previously associated and verified a TOTP token can continue to use it for MFA if the software token MFA is later disabled for the user pool. To make use of one of these youll need Azure AD Premium P1 or P2 license. As smartphones usually dont come with built-in MFA authenticators users have to install apps that provide this functionality. It is easier to duplicate a software token than a hardware token.
 Source: blog.identityautomation.com
Source: blog.identityautomation.com
With classic OATH tokens for Azure MFA with hard-coded secret keys such as Protectimus Two and Protectimus Crystal. There are hardware MFA such as RSA tokens that generate codes. Duos D-100 tokens have an expected minimum battery lifetime of 2 years. Associate software token to the user. After a detailed study on cognito with boto3 Python i found a solution to enable Software MFA.
 Source: securenvoy.com
Source: securenvoy.com
I want to create a AWSCognitoUserPool with only the SOFTWARE_TOKEN_MFA enabled for MFA using a Cloudformation template. MFA basics A simple password doesnt cut it for most systems especially ones with higher risks or sensitivity attached to them. Apps are software which means that wed be using software tokens. With classic OATH tokens for Azure MFA with hard-coded secret keys such as Protectimus Two and Protectimus Crystal. In Software Token authentication an authenticator app is installed on your smartphone and produces a string of 6-8 digit codes every time the user tries to log in with an MFA-enabled application.
 Source: jasonsamuel.com
Source: jasonsamuel.com
They have their pros and cons. A premium Azure license is not required. To assign the tokens to users edit that file to add your users user principal names usually their email address and then upload it to Azure Porta l Azure Active Directory MFA Server OATH tokens. The next step was to steal an RSA SecureID Software Token. Software based MFA such as Authy and Microsoft Authenticator do allow you to store backup in the cloud so it resolves the lostchange phone issue.
 Source: docs.microsoft.com
Source: docs.microsoft.com
With classic OATH tokens for Azure MFA with hard-coded secret keys such as Protectimus Two and Protectimus Crystal. Software based MFA such as Authy and Microsoft Authenticator do allow you to store backup in the cloud so it resolves the lostchange phone issue. Generally the authenticator apps work on a shared secret key known by the. They have their pros and cons. They have to put the code generated to access the data or application.
 Source: doubleoctopus.com
Source: doubleoctopus.com
Configuring TOTP for your user is a multi-step process where your user receives a secret code that they validate by entering a one-time password. As the name suggests multi-factor authentication MFA is the use of multiple factors to confirm the identity of someone who is requesting access to an application website or other resource. AWS Cognito TOTP Software Token MFA Using Java Configuring TOTP for your user is a multi-step process where your user receives a secret code that they validate by entering a one-time password. The design and dimensions of this Microsoft Office 365 MFA hardware token are also a factor in its popularity. Make sure to use the format described in the docs the secret is in base 32.
 Source: docs.microsoft.com
Source: docs.microsoft.com
A premium Azure license is not required. It is easier to duplicate a software token than a hardware token. Apps are software which means that wed be using software tokens. As smartphones usually dont come with built-in MFA authenticators users have to install apps that provide this functionality. Software based MFA such as Authy and Microsoft Authenticator do allow you to store backup in the cloud so it resolves the lostchange phone issue.

It is easier to duplicate a software token than a hardware token. They have their pros and cons. Multi-factor authentication is the difference between for example entering a password to gain access and entering a password plus a one-time password OTP or a password plus the answer to a security. Streamlined end-user MFA experience Office 365 SAML Connector Standard SAML 20 integration via Active Directory Authentication Libraries ADAL Supports newer web and rich clients such as Office 2013 and subsequent editions Office 365 STS Connector Security Token Service STS model with Web Services Federation WS-Federation. When I was checking them the vendor listed the SKUs with battery life listed in years.
 Source: javacodestuffs.com
Source: javacodestuffs.com
As the name suggests multi-factor authentication MFA is the use of multiple factors to confirm the identity of someone who is requesting access to an application website or other resource. Users who have previously associated and verified a TOTP token can continue to use it for MFA if the software token MFA is later disabled for the user pool. They have their pros and cons. Generally the authenticator apps work on a shared secret key known by the. Duos D-100 tokens have an expected minimum battery lifetime of 2 years.
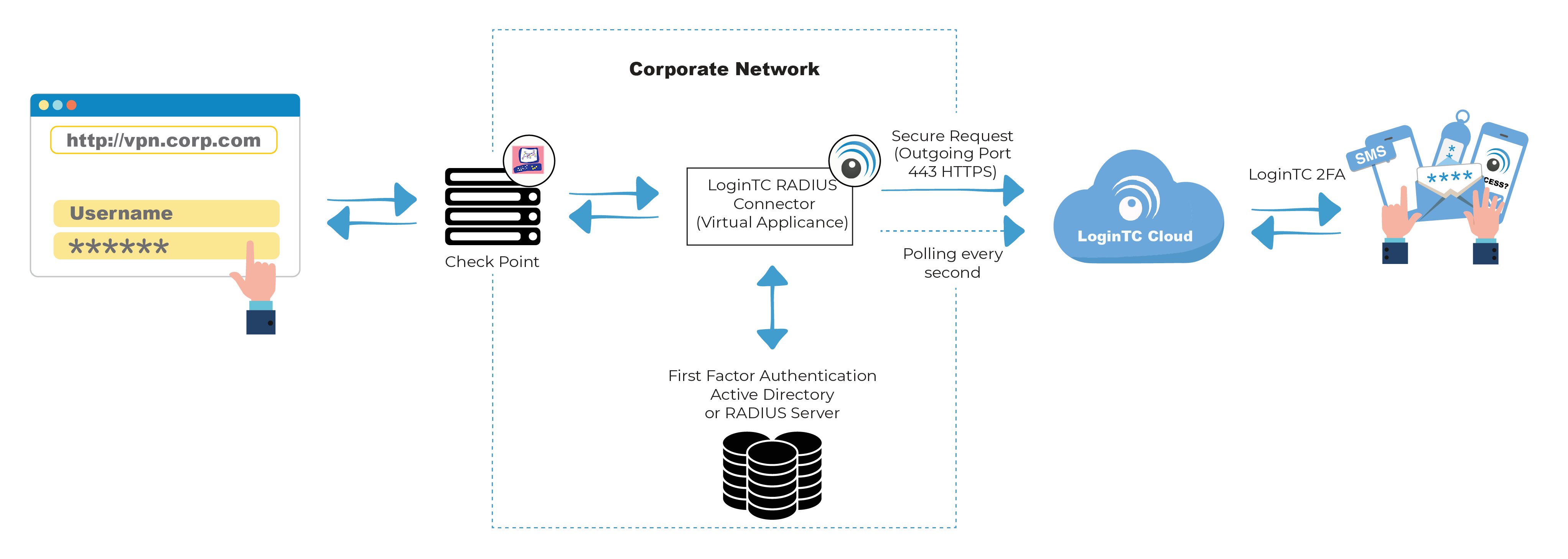 Source: logintc.com
Source: logintc.com
Hardware Tokens MFA Agents macOS Microsoft Windows SecurID SDK Software Tokens Android Blackberry Blackberry 10 iOS macOS Token Converter Windows Windows Phone Downloads Authentication Agents API SDK Apache Web Server Citrix StoreFront IIS Web Server Microsoft AD FS Microsoft Windows PAM Authentication Engine Authentication Manager Cloud. Also keep the header row in the file. However when specifying only SOFTWARE_TOKEN_MFA as the enabled MFA without any SMS the configuration should be. After a detailed study on cognito with boto3 Python i found a solution to enable Software MFA. Hence we should focus on using smartphones as MFA devices.
 Source: rcdevs.com
Source: rcdevs.com
Order Tokens Directly from Duo. The design and dimensions of this Microsoft Office 365 MFA hardware token are also a factor in its popularity. Order Tokens Directly from Duo. Verify the token received from the use. They are only available in.
 Source: aspectra.ch
Source: aspectra.ch
To protect your data with our OATH hardware token for Office 365 MFA you need to own an Office 365 subscription with 2-factor authentication on and an NFC Android phone. This type of token is used to generate valid one-time codes for MFA purposes. I want to create a AWSCognitoUserPool with only the SOFTWARE_TOKEN_MFA enabled for MFA using a Cloudformation template. Software based MFA such as Authy and Microsoft Authenticator do allow you to store backup in the cloud so it resolves the lostchange phone issue. Use otpauth to make the secret code into a qrcode.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title software token mfa by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.