Your Software token definition images are ready. Software token definition are a topic that is being searched for and liked by netizens now. You can Download the Software token definition files here. Find and Download all royalty-free photos and vectors.
If you’re looking for software token definition pictures information related to the software token definition keyword, you have come to the right blog. Our site frequently gives you suggestions for downloading the highest quality video and image content, please kindly hunt and locate more informative video content and images that fit your interests.
Software Token Definition. Examples include a wireless keycard opening a locked door or in the case of a customer trying to access their bank account online the use of a bank-provided token can. The token is used in addition to or in place of a password. Unlike cryptocurrencies they cannot be. The number of consumed tokens is specific to each feature and is apparent in the featureIncrement line in the license file.
 Tokenomics A Business Guide To Token Usage Utility And Value From pinterest.com
Tokenomics A Business Guide To Token Usage Utility And Value From pinterest.com
The number of consumed tokens is specific to each feature and is apparent in the featureIncrement line in the license file. Only a Super Admin can add software token profiles to the deployment. Traditionally a security token has been a hardware device that produces a new secure and individual PIN for each use and displays it on a built-in LCD display. Answer 1 of 8. A token is a device that employs an encrypted key for which the encryption algorithmthe method of generating an encrypted passwordis known to a networks authentication server. Stackoverflow had a pretty decent answer to this here.
A software token refer to.
A programming token is the basic component of source code. In this case the something is the fact the the user is authenticated and the token represents this fact. In a compiler an early step is to break the source up into tokens like a. Entry 1 of 2 1 a. Examples include a wireless keycard opening a locked door or in the case of a customer trying to access their bank account online the use of a bank-provided token can. 1 constants 2 identifiers 3 operators 4 separators and 5.
 Source: pinterest.com
Source: pinterest.com
A token is a device that employs an encrypted key for which the encryption algorithmthe method of generating an encrypted passwordis known to a networks authentication server. One-time password tokens are often used as a part of two-factor and multifactor authentication. 1 constants 2 identifiers 3 operators 4 separators and 5. Traditionally a security token has been a hardware device that produces a new secure and individual PIN for each use and displays it on a built-in LCD display. This token is then used in subsequent requests.
 Source: pinterest.com
Source: pinterest.com
The software tokens can be. In a compiler an early step is to break the source up into tokens like a. Unlike cryptocurrencies they cannot be. There are five categories of tokens. When a feature is checked-out a certain amount of tokens are consumed.
 Source: hideez.com
Source: hideez.com
The software tokens can be. A programming token is the basic component of source code. In programming a token is a single element of a programming language. Download Software Token Device Definition Type swtd files to be customized. A security token is a peripheral device used to gain access to an electronically restricted resource.
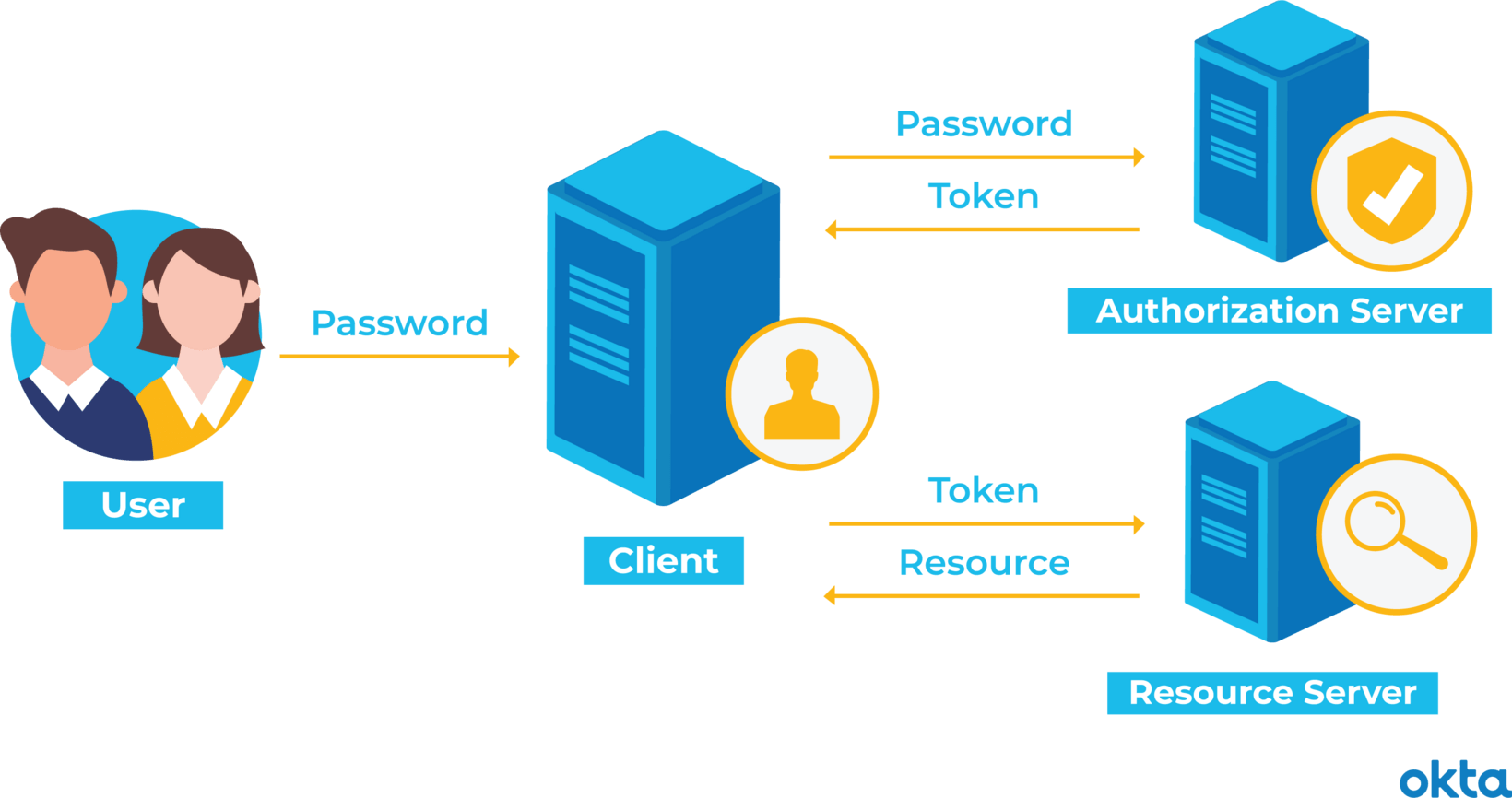 Source: okta.com
Source: okta.com
Examples include a wireless keycard opening a locked door or in the case of a customer trying to access their bank account online the use of a bank-provided token can. Entry 1 of 2 1 a. A software token profile is required for each platform for which you plan to distribute software tokens. Traditionally a security token has been a hardware device that produces a new secure and individual PIN for each use and displays it on a built-in LCD display. Ein Software- oder Soft-Token ist eine Software die Einmalpasswörter erstellt.
 Source: in.pinterest.com
Source: in.pinterest.com
If your organization uses a software token soft token application such as RSA SecurID to implement two-factor authentication users are required to first open their software token app and enter their PIN to obtain a passcode then enter the passcode in their. The software tokens can be. There are both software and hardware tokens. Normalerweise sind Sicherheits-Token kleine Hardware-Geräte die auf ihrem eingebauten LCD-Bildschirm sichere und. A piece resembling a coin issued as money by some person or body other than a de jure government.
 Source: pinterest.com
Source: pinterest.com
A unique software or hardware object given to a specific user to prove his or her identity. Normalerweise sind Sicherheits-Token kleine Hardware-Geräte die auf ihrem eingebauten LCD-Bildschirm sichere und. Ein Software- oder Soft-Token ist eine Software die Einmalpasswörter erstellt. When the system has authenticated the user instead of repeating this process for every request a token is created that represents the fact that the user is authenticated. In a compiler an early step is to break the source up into tokens like a.

There are both software and hardware tokens. A piece resembling a coin issued for use as for fare on a bus by a particular group on specified terms. A programming token is the basic component of source code. Ein Software- oder Soft-Token ist eine Software die Einmalpasswörter erstellt. Authentication tokens that are not physically tangible but exist as software on common devices for example computers or phones.
 Source: doubleoctopus.com
Source: doubleoctopus.com
A software token profile is required for each platform for which you plan to distribute software tokens. Unlike cryptocurrencies they cannot be. Traditionally a security token has been a hardware device that produces a new secure and individual PIN for each use and displays it on a built-in LCD display. Entry 1 of 2 1 a. Soft tokens Software token Soft token are just that.
 Source: techtarget.com
Source: techtarget.com
In programming a token is a single element of a programming language. This token is then used in subsequent requests. Software tokens attempt to emulate hardware tokens which are physical tokens needed for two-factor authentication systems and there are both advantages and disadvantages to. A soft token is a software version of a hard token which is a security device used to give authorized users access to secure locations or computer systems. The token is used in addition to or in place of a password.
 Source: pinterest.com
Source: pinterest.com
Hard tokens Hardware token Hard Token are physical devices used to gain access to an electronically restricted resource. Unlike cryptocurrencies they cannot be. A security token is a peripheral device used to gain access to an electronically restricted resource. Normalerweise sind Sicherheits-Token kleine Hardware-Geräte die auf ihrem eingebauten LCD-Bildschirm sichere und. A programming token is the basic component of source code.
 Source: metaco.com
Source: metaco.com
Use a software token application for two-factor authentication for GlobalProtect. Edit the file to change Device and Token names and any other changes or defaults needed. A software token profile is required for each platform for which you plan to distribute software tokens. It acts like an electronic key to access something. A programming token is the basic component of source code.
 Source: pinterest.com
Source: pinterest.com
Hard tokens Hardware token Hard Token are physical devices used to gain access to an electronically restricted resource. One-time password tokens are often used as a part of two-factor and multifactor authentication. It acts like an electronic key to access something. A soft token is a software-based security token that generates a single-use login PIN. A one-time password token OTP token is a security hardware device or software program that is capable of producing a single-use password or PIN passcode.
 Source: curity.io
Source: curity.io
Normalerweise sind Sicherheits-Token kleine Hardware-Geräte die auf ihrem eingebauten LCD-Bildschirm sichere und. If your organization uses a software token soft token application such as RSA SecurID to implement two-factor authentication users are required to first open their software token app and enter their PIN to obtain a passcode then enter the passcode in their. Characters are categorized as one of five classes of tokens that describe their functions constants identifiers operators reserved words and separators in accordance with the rules of the programming language. A software token refer to. Soft tokens Software token Soft token are just that.
 Source: pinterest.com
Source: pinterest.com
A token is a device that employs an encrypted key for which the encryption algorithmthe method of generating an encrypted passwordis known to a networks authentication server. A unique software or hardware object given to a specific user to prove his or her identity. There are five categories of tokens. Unlike cryptocurrencies they cannot be. For this reason soft tokens can be called virtual tokens since they are a virtual version of hardware keys and other physical security devices.
 Source: nl.pinterest.com
Source: nl.pinterest.com
There are both software and hardware tokens. Without the correct token a user cannot access any computer system requiring it. Authentication tokens that are not physically tangible but exist as software on common devices for example computers or phones. Soft tokens Software token Soft token are just that. Characters are categorized as one of five classes of tokens that describe their functions constants identifiers operators reserved words and separators in accordance with the rules of the programming language.
 Source: pinterest.com
Source: pinterest.com
In this case the something is the fact the the user is authenticated and the token represents this fact. A soft token is a software-based security token that generates a single-use login PIN. A programming token is the basic component of source code. Examples include a wireless keycard opening a locked door or in the case of a customer trying to access their bank account online the use of a bank-provided token can. The software tokens can be.
 Source: pinterest.com
Source: pinterest.com
Unlike cryptocurrencies they cannot be. In processing source code eg. A token is a device that employs an encrypted key for which the encryption algorithmthe method of generating an encrypted passwordis known to a networks authentication server. Non-fungible tokens or NFTs are cryptographic assets on blockchain with unique identification codes and metadata that distinguish them from each other. Use a software token application for two-factor authentication for GlobalProtect.
Source: encrypted-tbn0.gstatic.com
The software tokens can be. When a feature is checked-out a certain amount of tokens are consumed. 1 constants 2 identifiers 3 operators 4 separators and 5. Download Software Token Device Definition Type swtd files to be customized. A unique software or hardware object given to a specific user to prove his or her identity.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title software token definition by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.