Your Software keylogger attack images are ready. Software keylogger attack are a topic that is being searched for and liked by netizens now. You can Find and Download the Software keylogger attack files here. Get all royalty-free images.
If you’re looking for software keylogger attack pictures information connected with to the software keylogger attack keyword, you have pay a visit to the ideal site. Our site frequently provides you with hints for viewing the highest quality video and image content, please kindly hunt and locate more informative video content and images that match your interests.
Software Keylogger Attack. As its name indicates key-logger this term refers to a malicious computer program that secretly records every keystroke made by a computer user. Software keyloggers are computer programs that record every keystroke made on the keyboard. While keyloggers primary objective is to track the keyboard behaviour of a user they now have capabilities that extend beyond that feature. At present keyloggers together with phishing and social engineering methods are one of the most commonly used methods of cyber fraud.
 Detecting Keyloggers On Dynamic Analysis Systems Lastline From lastline.com
Detecting Keyloggers On Dynamic Analysis Systems Lastline From lastline.com
What is a keylogger. A kernel mode keylogger is a more powerful and complex software keylogging method. What is a keylogger. Keyloggers are activity-monitoring software programs that give hackers access to your. You enter sensitive data onto your keyboard believing nobody is watching. Instead of real documents the emails had the Olympic Vision keylogger attached.
Kernel Keylogger Attacks - Kernel mode keyloggers are the most common type of keylogging software and theyre also the hardest to detect.
In fact keylogging software is hard at work logging everything that you type. As we all know most anti-keylogger software is designed to scramble keyboard keystrokes. These keyloggers require the attacker to actively monitor each keypress. Keyloggers are activity-monitoring software programs that give hackers access to your. Keyloggers are commonly referred to as tracking software software for controlling user operation controlling keystroke. The perpetrators of this cyber attack were finally identified in October 2018 when it was also revealed that they had stolen more than 4 million since the launch of the attack.
Source:
Software keyloggers are computer programs that record every keystroke made on the keyboard. It is only periodically sharing the information and is a manual transfer of information by a human agent. Software that logs what you type on your keyboard. Install Key Encryption Software. A keylogger or keystroke logger is a type of software or hardware used to track and record what someone types on their keyboard.
 Source: enterprise.comodo.com
Source: enterprise.comodo.com
Systems keystroke recorders keystroke loggers keyboard sniffers and snoop ware. Whats a keylogger. Theyre exploiting vulnerabilities with a range of malware exploits like a keylogger attack. In fact keylogging software is hard at work logging everything that you type. As we all know most anti-keylogger software is designed to scramble keyboard keystrokes.
 Source: digitalguyde.com
Source: digitalguyde.com
Kernel keyloggers use filter drivers to intercept privileged access credentials. Keyloggers or keystroke loggers are software programs or hardware devices that track the activities keys pressed of a keyboard. A Software Keylogger is a type of keylogging tool that needs to be directly or remotely installed on the target machine. It works with higher privileges and can be harder to locate in a system. Software keyloggers are computer programs that record every keystroke made on the keyboard.
 Source: researchgate.net
Source: researchgate.net
This is a hardware keylogger attack. What is a keylogger. Theyre exploiting vulnerabilities with a range of malware exploits like a keylogger attack. As we all know most anti-keylogger software is designed to scramble keyboard keystrokes. Keystroke logging software is one of the oldest forms of malware dating back to typewriters.
 Source: promon.co
Source: promon.co
At present keyloggers together with phishing and social engineering methods are one of the most commonly used methods of cyber fraud. There are lots of software available in market which make a Keylogger undetectable by latest antivirus we are going to study about them too in upcoming chapters There are many keyloggers available in market with various features. It works with higher privileges and can be harder to locate in a system. Keyloggers are used to gain fraudulent access to confidential information such as. Software keyloggers are computer programs that record every keystroke made on the keyboard.
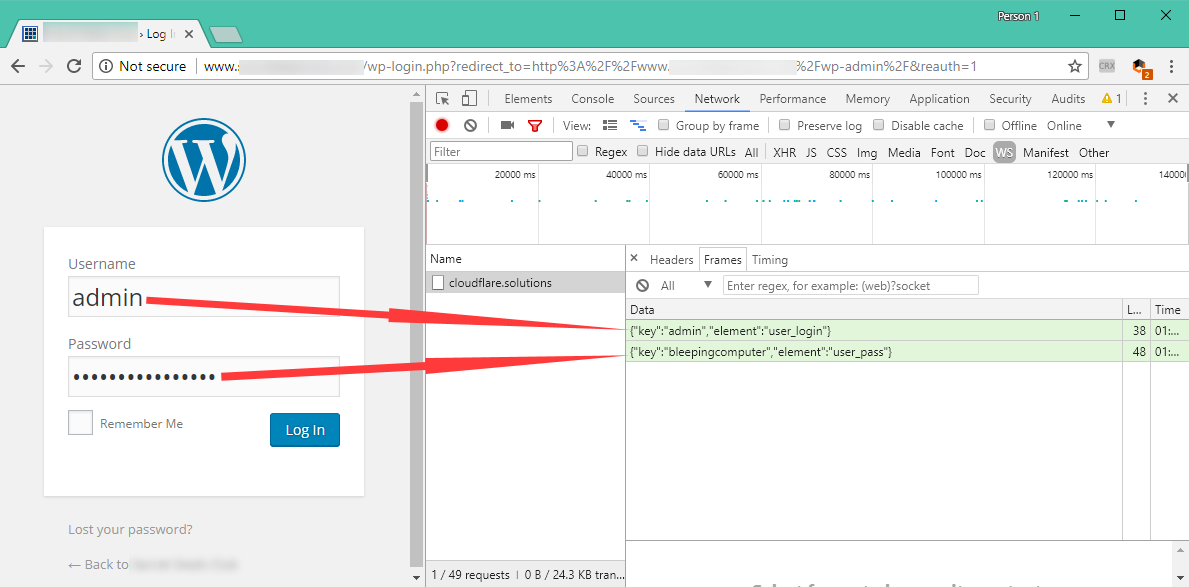 Source: bleepingcomputer.com
Source: bleepingcomputer.com
Keystroke logging software is one of the oldest forms of malware dating back to typewriters. These keyloggers require the attacker to actively monitor each keypress. This is a software keylogger attack as screenshots video captures and keystrokes have been. When a hardware keylogger intercepts the keys it can only record random characters. The term keylogger or keystroke logger is self-explanatory.
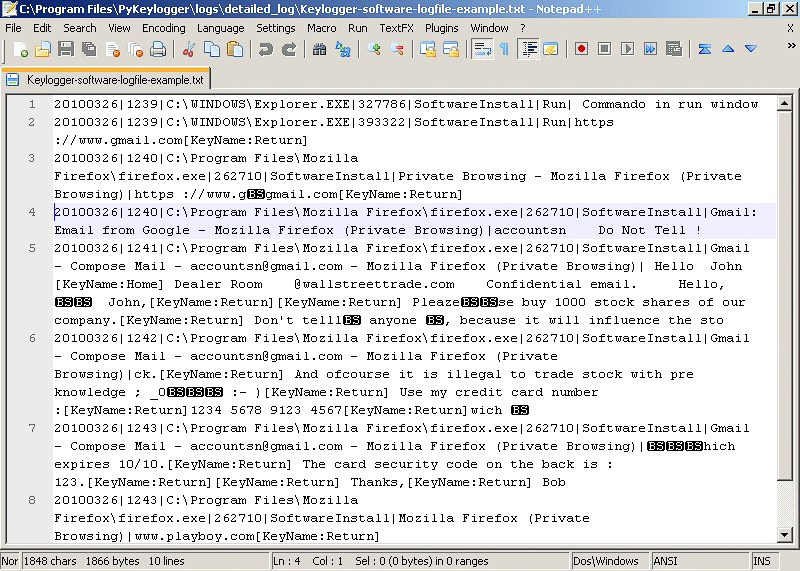 Source: educalingo.com
Source: educalingo.com
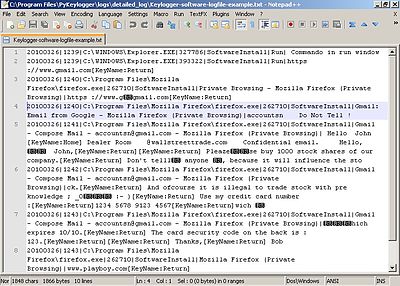
Software that logs what you type on your keyboard. Instead of real documents the emails had the Olympic Vision keylogger attached. It is only periodically sharing the information and is a manual transfer of information by a human agent. This is a software keylogger attack as it is sharing the information every three hours to the attacker. What Is Keylogging Attack.
 Source: wikiwand.com
Source: wikiwand.com
As its name indicates key-logger this term refers to a malicious computer program that secretly records every keystroke made by a computer user. Someone who wants to monitor activity on a specific machine can download the keylogger intentionally or the program can be downloaded as malware and operated as part of a rootkit or remote administration Trojan RAT system without the user realizing that they put their devices at risk. Keyloggers can be used legally some people even install them on their own devices and you may have even used a computer with software installed to log keystrokes for monitoring and ensuring safe or approved use. Keyloggers are used to gain fraudulent access to confidential information such as. Cyber threats such as keylogging attacks date back to the early days of the internet.
 Source: zdnet.com
Source: zdnet.com
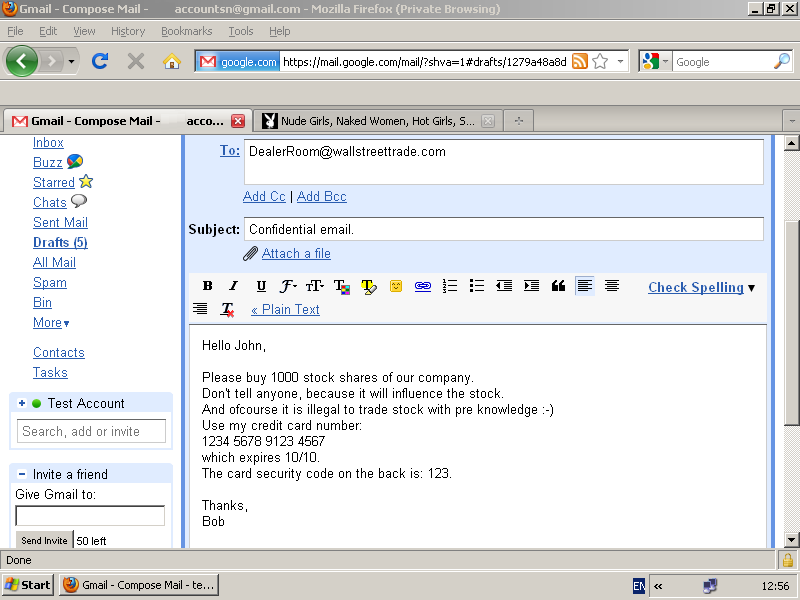
Kernel keyloggers use filter drivers to intercept privileged access credentials. At present keyloggers together with phishing and social engineering methods are one of the most commonly used methods of cyber fraud. Software that logs what you type on your keyboard. Even though keylogger developers market their products as legitimate software most keyloggers can be used to steal personal user data and in political and industrial espionage. Using a Keylogger an attacker can remotely get to know.
 Source: enterprise.comodo.com
Source: enterprise.comodo.com
The perpetrators of this cyber attack were finally identified in October 2018 when it was also revealed that they had stolen more than 4 million since the launch of the attack. Once a software keylogger has been installed it can be used for any of the following types of cyberattacks. Software that logs what you type on your keyboard. Kernel mode keyloggers use filter drivers that can intercept keystrokes. Install Key Encryption Software.

Software keyloggers are computer programs that record every keystroke made on the keyboard. A keylogger or keystroke logger is a type of software or hardware used to track and record what someone types on their keyboard. A keylogger is an insidious form of spyware. Malware USB sticks and software and. This is a software keylogger attack as it is sharing the information every three hours to the attacker.
 Source: enterprise.comodo.com
Source: enterprise.comodo.com
Instead of real documents the emails had the Olympic Vision keylogger attached. Kernel keyloggers use filter drivers to intercept privileged access credentials. By this process the keylogger will be removed forever from your computer and you become safe from the hacker attack. This is a hardware keylogger attack. Systems keystroke recorders keystroke loggers keyboard sniffers and snoop ware.
 Source: softactivity.com
Source: softactivity.com
Its invisible to the victims eye therefore heshe wont even imagine that someone might be spying on their actions. Using a Keylogger an attacker can remotely get to know. Someone who wants to monitor activity on a specific machine can download the keylogger intentionally or the program can be downloaded as malware and operated as part of a rootkit or remote administration Trojan RAT system without the user realizing that they put their devices at risk. A keylogger is an insidious form of spyware. Key encryption software also prevents a hardware keylogger attack by encrypting the keys you type on the keyboard.
Source: encrypted-tbn0.gstatic.com
A keylogger or keystroke logger is a type of software or hardware used to track and record what someone types on their keyboard. Its still popular and often used as part of larger cyber attacks. If you want extra protection against a hardware keylogger key encryption software is an effective tool. However they are not designed to detect and remove them from your system. Kernel mode keyloggers use filter drivers that can intercept keystrokes.
 Source: resources.infosecinstitute.com
Source: resources.infosecinstitute.com
The program reads and logs keystrokes and it can identify patterns to help you find your password. Keyloggers are a form of spyware where users are unaware their actions are being tracked. There are lots of software available in market which make a Keylogger undetectable by latest antivirus we are going to study about them too in upcoming chapters There are many keyloggers available in market with various features. Software keyloggers are computer programs that record every keystroke made on the keyboard. What is a keylogger.
 Source: ultimatepopculture.fandom.com
Source: ultimatepopculture.fandom.com
Cyber threats such as keylogging attacks date back to the early days of the internet. This is a hardware keylogger attack. This malware program is not very sophisticated but for the purpose of these attacks it doesnt need to be. Theyre exploiting vulnerabilities with a range of malware exploits like a keylogger attack. Keylogger can be either a software programme or a hardware that is used by an attacker to record the key presses on a users keyboard.
 Source: avast.com
Source: avast.com
Keyloggers or keystroke loggers are software programs or hardware devices that track the activities keys pressed of a keyboard. Install Key Encryption Software. This is a software keylogger attack as it is sharing the information every three hours to the attacker. Instead of real documents the emails had the Olympic Vision keylogger attached. A Software Keylogger is a type of keylogging tool that needs to be directly or remotely installed on the target machine.
 Source: avast.com
Source: avast.com
Keystroke logging software is one of the oldest forms of malware dating back to typewriters. Keyloggers are used to gain fraudulent access to confidential information such as. When a hardware keylogger intercepts the keys it can only record random characters. A keylogger or keystroke logger is a type of software or hardware used to track and record what someone types on their keyboard. These keyloggers require the attacker to actively monitor each keypress.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title software keylogger attack by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.