Your I2 software intelligence images are ready in this website. I2 software intelligence are a topic that is being searched for and liked by netizens today. You can Download the I2 software intelligence files here. Get all free images.
If you’re looking for i2 software intelligence images information linked to the i2 software intelligence topic, you have visit the right blog. Our site frequently gives you suggestions for viewing the highest quality video and picture content, please kindly hunt and locate more informative video articles and images that fit your interests.
I2 Software Intelligence. I2 received a rating of 41 from ITQlick team. Analysts Notebook part of the i2 Clarity Platform delivers the richest assisted analysis and visualization capabilities in the world to support analysts in quickly turning large sets of disparate information into high-quality and actionable intelligence to prevent crime and terrorism. IBM Security i2 arms analysts with the advanced analytics and threat intelligence analysis capabilities they need to detect disrupt and defeat physical and cyber threats coming at them with increasing speed and sophistication. New ideals challenge sovereignty and rapid technical advancements.
 Law Enforcement Investigative And Intelligence Analysis With I2 Ibm From ibm.com
Law Enforcement Investigative And Intelligence Analysis With I2 Ibm From ibm.com
IBM i2 Enterprise Insight Analysis helps analysts and investigators turn overwhelming and disparate data sets into comprehensive intelligence in near real-time. Palantir is a very pretty interface which can provide some useful information. I2 is a fast growing cloud-based Security software it is designed to support small medium and large size business. Software For National Intelligence Agencies. About i2 Inc. At CodeCenters we have been working with link analysis methods for over 20 years and we have been using i2 and in-house custom linking software for most of that time.
IBM Security i2 Enterprise Insight Analysis helps your organization turn overwhelming and disparate data into actionable insight and intelligence in near real time.
IBM i2 Information Store. The Leadership Team at i2 have been leading transformation projects for over 25 years and have. With almost two decades of i2 training experience around the world Blue Light is the premier source of training for the entire IBM i2 software. I2 received a rating of 41 from ITQlick team. Palantir is a very pretty interface which can provide some useful information. Answer 1 of 2.
 Source: ibm.com
Source: ibm.com
Palantir is a very pretty interface which can provide some useful information. And export-import based integrations with. With almost two decades of i2 training experience around the world Blue Light is the premier source of training for the entire IBM i2 software. Link Analysis software helps organizations efficiently piece together disparate data into a single cohesive intelligence picture. FounderCPO Sirenio - ELK for investigative intelligence.
 Source: hu.pinterest.com
Source: hu.pinterest.com
IBM i2 Analysts Notebook. For analysts DataWalk provides a single repository effectively an embedded intelligence database - for all desired data along with. IBM i2 Information Store. I remember disliking the lack of control over how things were interpreted by the system as well. The IBM i2 Intelligence Analysis portfolio provides government law enforcement defense national security and commercial organizations around the world with innovative and advanced human-led threat analysis tools to help generate actionable intelligence to detect disrupt and prevent physical and cyber threats.
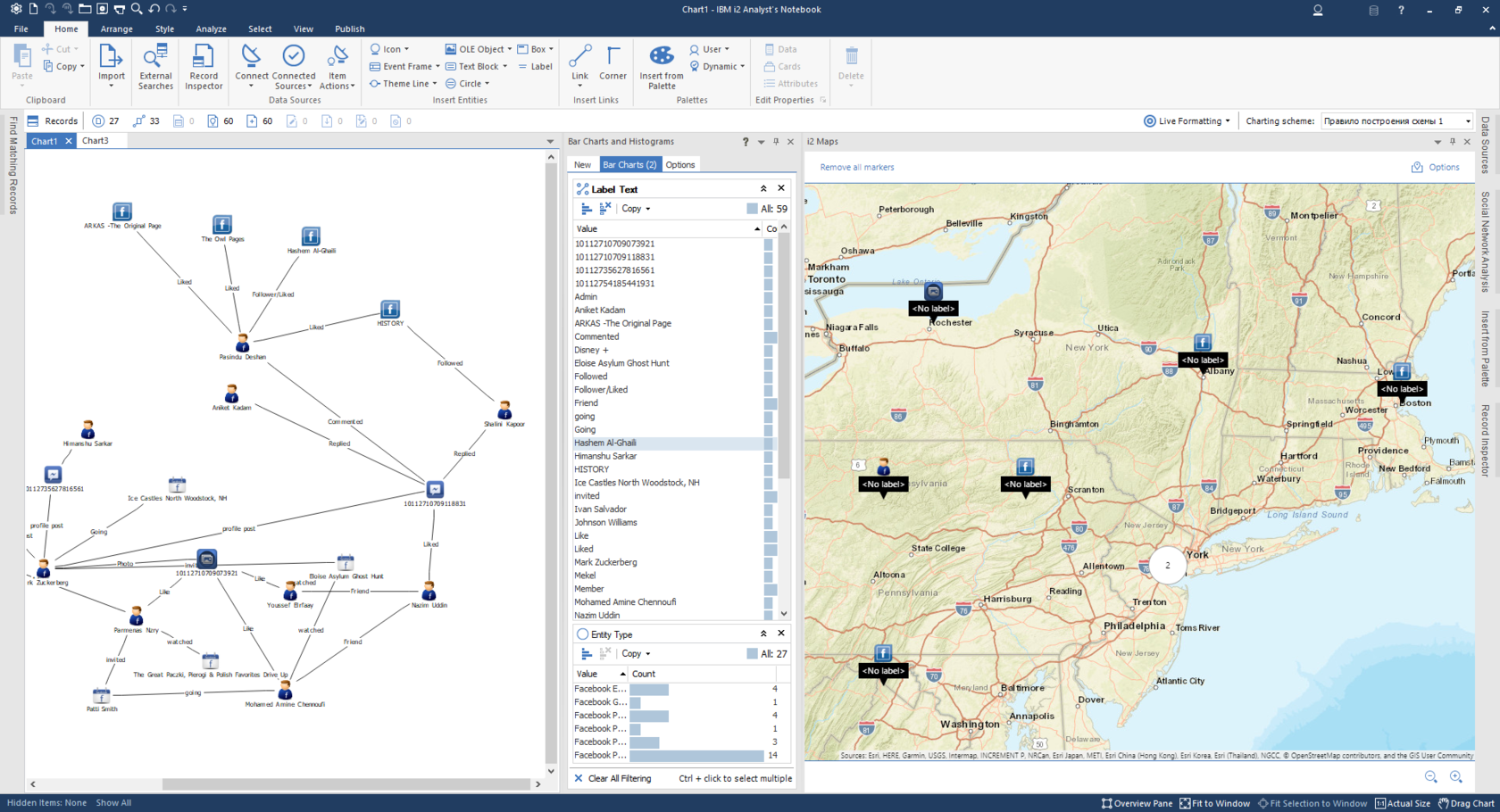 Source: sociallinks.io
Source: sociallinks.io
FounderCPO Sirenio - ELK for investigative intelligence. About i2 Inc. I remember disliking the lack of control over how things were interpreted by the system as well. Experienced i2 software trainer intelligence analyst and consultant providing services to both private- and public-sector organisations. Analysts Notebook part of the i2 Clarity Platform delivers the richest assisted analysis and visualization capabilities in the world to support analysts in quickly turning large sets of disparate information into high-quality and actionable intelligence to prevent crime and terrorism.
 Source: pinterest.com
Source: pinterest.com
Answer 1 of 2. I2 is the leading worldwide provider of visual investigative analysis software for law enforcement government military intelligence and commercial organizations. For analysts DataWalk provides a single repository effectively an embedded intelligence database - for all desired data along with. The software cost is considered average 31. The IBM i2 Intelligence Analysis portfolio provides government law enforcement defense national security and commercial organizations around the world with innovative and advanced human-led threat analysis tools to help generate actionable intelligence to detect disrupt and prevent physical and cyber threats.
 Source: pinterest.com
Source: pinterest.com
Amazon EC2 instances powered by AMD EPYC provide your compute workloads with the performance they need. We work with governments executives business users and analytics teams by creating the right. I2 Enabled A Modern Analytics Advisory Services and Product Company. I2 iSquared was founded in 2019 bringing together a unique blend of consultancy business technical and transformational expertise and building upon a proven track record of multi-billion dollar transformation project delivery. IBM i2 Information Store.
 Source: techcrunch.com
Source: techcrunch.com
IBM Security i2 Enterprise Insight Analysis helps your organization turn overwhelming and disparate data into actionable insight and intelligence in near real time. Since 2017 we have been helping companies plan design and build inclusive strategic solutions leveraging our expertise both in Data Analytics and Industry experience. I2 received a rating of 41 from ITQlick team. And export-import based integrations with. Todays enemies of the State are more intelligent distributed and adaptable than ever before.
 Source: pinterest.com
Source: pinterest.com
About i2 Inc. Palantir is a very pretty interface which can provide some useful information. Experienced i2 software trainer intelligence analyst and consultant providing services to both private- and public-sector organisations. About i2 Inc. I remember disliking the lack of control over how things were interpreted by the system as well.
 Source: ibm.com
Source: ibm.com
We work with governments executives business users and analytics teams by creating the right. Sintelix offers integrations with. From national security and defense to cyber and enterprise-wide threats the solution helps you develop a comprehensive understanding of your threat landscape to identify vulnerabilities and disrupt threats. IBM i2 Enterprise Insight Analysis helps analysts and investigators turn overwhelming and disparate data sets into comprehensive intelligence in near real-time. The software cost is considered average 31.
 Source: ibm.com
Source: ibm.com
Sintelix offers integrations with. The Industry-leading Provider of IBM i2 Training. Palantir is a very pretty interface which can provide some useful information. For analysts DataWalk provides a single repository effectively an embedded intelligence database - for all desired data along with. You can derive hidden connections and patterns buried in enterprise third party and public data sets.
 Source: pinterest.com
Source: pinterest.com
The Leadership Team at i2 have been leading transformation projects for over 25 years and have. I remember disliking the lack of control over how things were interpreted by the system as well. I2 Enabled A Modern Analytics Advisory Services and Product Company. You can derive hidden connections and patterns buried in enterprise third party and public data sets. IBM Security i2 arms analysts with the advanced analytics and threat intelligence analysis capabilities they need to detect disrupt and defeat physical and cyber threats coming at them with increasing speed and sophistication.
 Source: br.pinterest.com
Source: br.pinterest.com
Security and intelligence analysts are often at a loss to uncover hidden connections in disparate data from multiple sources and gain actionable intelligence quickly. The IBM i2 suite of software provides an enterprise intelligence analysis environment that facilitates information sharing and intelligence production. I remember disliking the lack of control over how things were interpreted by the system as well. Todays enemies of the State are more intelligent distributed and adaptable than ever before. Download Analysts Notebook for free.
 Source: pinterest.com
Source: pinterest.com
For analysts DataWalk provides a single repository effectively an embedded intelligence database - for all desired data along with. Software For National Intelligence Agencies. I offer 3 types of service which my clients mix match to suit their needs Classroom and One-To-One Training. The Industry-leading Provider of IBM i2 Training. Since 2017 we have been helping companies plan design and build inclusive strategic solutions leveraging our expertise both in Data Analytics and Industry experience.
 Source: ibm.com
Source: ibm.com
From national security and defense to cyber and enterprise-wide threats the solution helps you develop a comprehensive understanding of your threat landscape to identify vulnerabilities and disrupt threats. Palantir is a very pretty interface which can provide some useful information. IBM Software IBM i2 Fraud Intelligence Analysis - Insurance 5 Investigation management i2 Fraud Intelligence Analysis supports your internal processes. An IBM Gold Partner with more i2 Training expertise than any other company Blue Light focuses on. New ideals challenge sovereignty and rapid technical advancements.
 Source: linkurio.us
Source: linkurio.us
The Industry-leading Provider of IBM i2 Training. Answered 2 years ago. Expanding its portfolio of analytic software for state and local governments IBM is in the process of acquiring security analytics software provider i2 the companies announced Wednesday. IBM Software IBM i2 Fraud Intelligence Analysis - Insurance 5 Investigation management i2 Fraud Intelligence Analysis supports your internal processes. Todays enemies of the State are more intelligent distributed and adaptable than ever before.
 Source: pinterest.com
Source: pinterest.com
Experienced i2 software trainer intelligence analyst and consultant providing services to both private- and public-sector organisations. Download Analysts Notebook for free. IBM Security i2 arms analysts with the advanced analytics and threat intelligence analysis capabilities they need to detect disrupt and defeat physical and cyber threats coming at them with increasing speed and sophistication. With almost two decades of i2 training experience around the world Blue Light is the premier source of training for the entire IBM i2 software. The Leadership Team at i2 have been leading transformation projects for over 25 years and have.
 Source: pinterest.com
Source: pinterest.com
IBM Security i2 Enterprise Insight Analysis helps your organization turn overwhelming and disparate data into actionable insight and intelligence in near real time. IBM i2 Intelligence Analysis software aimed at law enforcement government or businesses looking to predict disrupt and prevent criminal terrorist and fraudulent activities. IBM i2 Enterprise Insight Analysis helps analysts and investigators turn overwhelming and disparate data sets into comprehensive intelligence in near real-time. I offer 3 types of service which my clients mix match to suit their needs Classroom and One-To-One Training. The software cost is considered average 31.
 Source: ibm.com
Source: ibm.com
Palantir is a very pretty interface which can provide some useful information. You can derive hidden connections and patterns buried in enterprise third party and public data sets. The Industry-leading Provider of IBM i2 Training. Download Analysts Notebook for free. If you want to analyze and get intelligence fraud troubleshooting LEA etc on large amounts of data eg.
 Source: ibm.com
Source: ibm.com
IBM i2 Enterprise Insight Analysis helps analysts and investigators turn overwhelming and disparate data sets into comprehensive intelligence in near real-time. Link Analysis software helps organizations efficiently piece together disparate data into a single cohesive intelligence picture. From national security and defense to cyber and enterprise-wide threats the solution helps you develop a comprehensive understanding of your threat landscape to identify vulnerabilities and disrupt threats. IBM i2 Intelligence Analysis software aimed at law enforcement government or businesses looking to predict disrupt and prevent criminal terrorist and fraudulent activities. You can derive hidden connections and patterns buried in enterprise third party and public data sets.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title i2 software intelligence by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.







